Intro to SSH - tutorial video
SSH - login
Tip
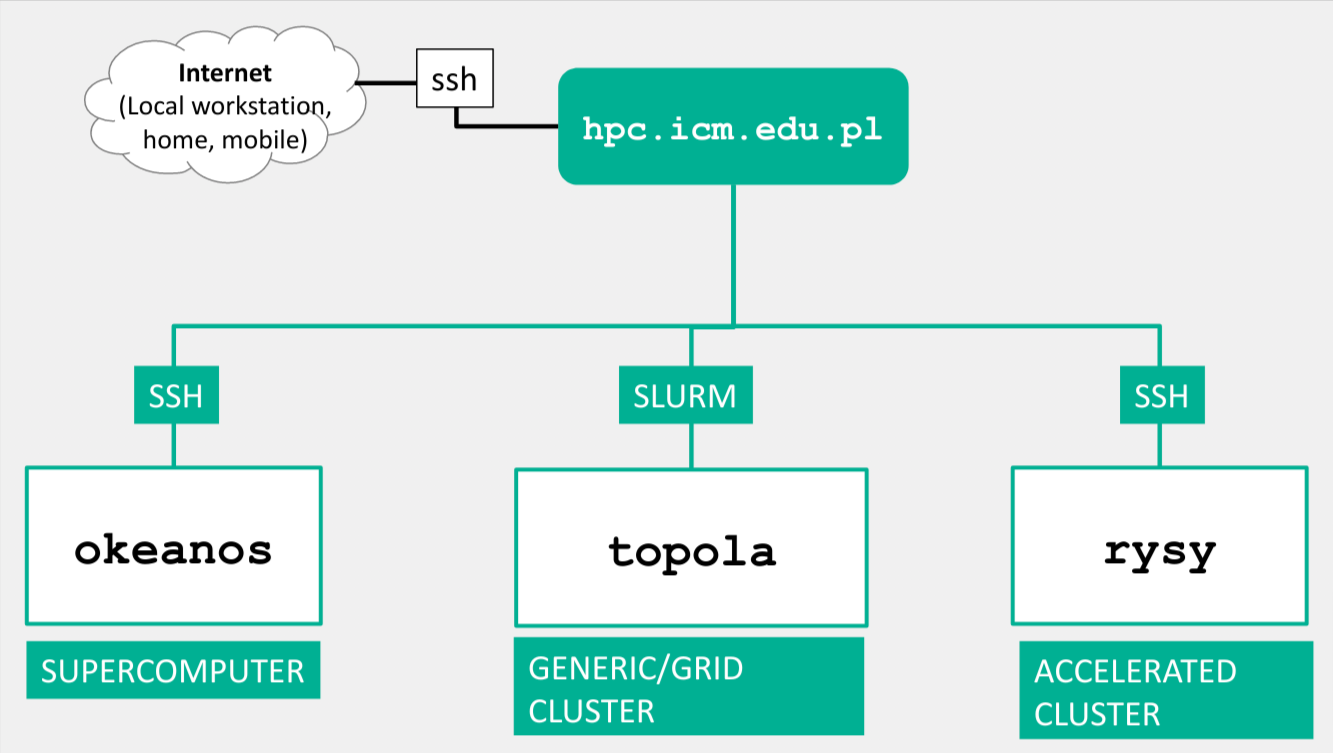
ICM login: ssh username@hpc.icm.edu.pl.
Logging in is done using a username (up to 8 letters, not an e-mail address).
On some systems, an additional login step is possible/required from the hpc.icm.edu.pl computer,
e.g. ssh rysy, ssh okeanos.
Info
From December 2020, logging in using the ssh protocol requires two-factor authentication (2FA - 2 Factors Authentication) with the use of TOTP (Time-based One-time Password) tokens.
Account name and password setting
When log in in for the first time, it is necessary to change the password.
Create SSH Keys
Logging in can be authenticated by entering a password or by using a cryptographic key. The keys are more secure (and more convenient - you don't have to type a password every time).
# To generate SSH keys on the local computer use the command:
ssh-keygen
# Then copy the public key to the target server:
ssh-copy-id -i ~/.ssh/mykey.pub user@your.server.example.com
# Only you (and no other user) should be able to read the keys:
chmod 400 ~ /.ssh/mykey
# If you want to use an existing key, don't forget to add it to 'ssh agent' on the local machine
ssh-add ~/.ssh/mykey
# if `ssh-add` fails saying `Could not open a connection to your authentication agent.` you have to start the ssh-agent
eval `ssh-agent -s`
# logging in
ssh user@your.server.example.com
# logging in in with a specific key
ssh -o IdentitiesOnly = yes -i ~ / .ssh / example_rsa user@your.server.example.com
# logging in in using a password (instead of a key)
ssh -o PubkeyAuthentication = no user@your.server.example.com
Digital signature of the hpc.icm.edu.pl access machine
When logging in, the user's computer makes sure that it connects to the authorized hpc.icm.edu.pl machine.
For this purpose, the cryptographic key imprint of the access machine is checked.
When connecting for the first time, you must agree to adding hpc.icm.edu.pl to your friends list.
ssh username@hpc.icm.edu.pl
The authenticity of host 'hpc.icm.edu.pl (2001: 6a0: 2001: 2321 :: 79)' can't be established.
ECDSA key fingerprint is SHA256: KGMfnzeNErKlS8J / MYOBsnFKFl95VJ + BFm4FAYwKV6A.
Are you sure you want to continue connecting (yes / no / [fingerprint])? yes
Warning: Permanently added 'hpc.icm.edu.pl' (ECDSA) to the list of known hosts.
OTP:
The procedure for removing the old keyprint is shown below.
Windows
Run the regedit program (Windows system application).
Then, in the panel on the left, search for an entry in the tree:
HKEY_CURRENT_USER \ Software \ UserName \ PuTTY \ SshHostKeys
and in the window on the right, find the line containing the name 'hpc.icm.edu.pl', and then delete it.
Linux
To delete the old key, run the following command in the terminal:
ssh-keygen -f $ HOME/.ssh/known_hosts -R hpc.icm.edu.pl
Password Manager
The [pass] program https://www.passwordstore.org/ is a password manager that allows linux users to safely store their passwords on the local computer. For example:
$ pass remote_computers / icm -c
Copied zdalne_kompociąg / icm is a clipboard. Will clear in 45 seconds.
Finishing work
When you are finished, log out with the command exit orlogout
or with the key combination Ctrl + D.
Support
User support and support for computational grants:
- E-mail: help (monkey) icm.edu.pl
- By phone: +48 22 8749 200